CryptoLocker Removal Tool
We jus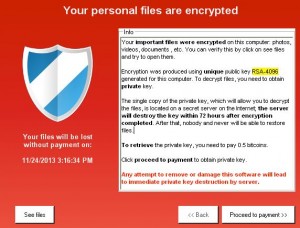 t recently found out that there is a way you can recover your files from the CryptoLocker Virus. FireEye and Fox-IT have somehow managed to gain access to the private encryption keys used by the CryptoLocker’s programmers. They were also able to reverse-engineer the virus code and create a website that will allow you to recover your files from this devastating virus.
t recently found out that there is a way you can recover your files from the CryptoLocker Virus. FireEye and Fox-IT have somehow managed to gain access to the private encryption keys used by the CryptoLocker’s programmers. They were also able to reverse-engineer the virus code and create a website that will allow you to recover your files from this devastating virus.
All you need to do to repair the CryptoLocker virus is go to , Enter your email address, and upload one of your infected files and then you will be presented with the decryption key necessary to unlock the rest of your files.
One small downfall is that if you have been infected by a variant of the CryptoLocker virus this fix may not work. Variants start out as the same virus and then are modified to meet the wants and needs of that particular programmer.
How do you get the CryptoLocker virus? The virus is can be received in many ways, but the ones we have worked on are coming through as email attachments. For example: “UPS Shipment”, “Paypal”, “Tax Updates”, or any ZIP file extension. This may come from someone you know if they have been infected with malware or another virus.
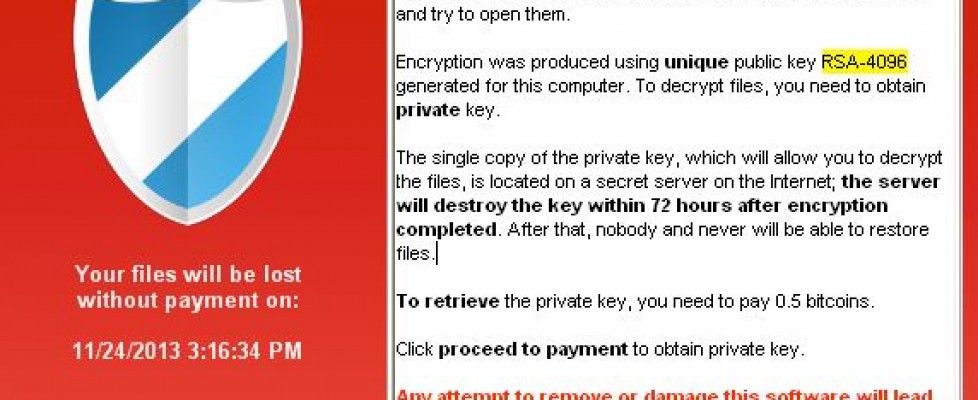
What does the CryptoLocker affect? The virus adds cryptography to all of the word documents, excel, pictures, mp3, text documents and .ini files. The CryptoLocker virus will even seek out files on your network drives. One thing we have come across is that the virus will only affect what you have access to. If you are denied access to a drive on the network it will not be able to reach any files on that drive. You will know that the file in infected because it will give you a pop-up that says this file has been protected or locked. The pop-up will usually be a red screen that will say “Your personal files are encrypted” and show you a countdown clock. The countdown clock shows when your price to buy the key goes up. So if you do not purchase the $300’s in Bitcoin’s or Moneypak to fix the virus $300 will go up.
The virus infects the files by making a copy of the file, injecting the cryptography and then deleting the original file. By the time you figure out that you have the virus, it is too late. If you are lucky enough to find the originating computer before it spreads to your network, you can save yourself a ton of work. Since this procedure works in the background it is totally undetectable until someone opens up an infected file.
How to figure out who has a virus on the network? So far this has been pretty easy for us to tell who the culprit has been. In all of our cases we could deduce the person who had the virus because their personal drive on the network had the viruses. When we setup a network our default settings we assign a user drive that syncs with their “My Documents” directory. By doing folder syncing the files are always safe on the server if the laptop were to get stolen or broken, plus their files are backed up via the backup utility. (One caveat: This can be a pain in the rump with the new MS Outlook because it stores the PST in the My Documents folder, which you will have to relocate back to the old directory in the “users” directory.) One could also deduce the person with the virus by figuring out the access rights to the drives that were infected.
Before the fix was available, you had three options. 1. Pay the Money, 2. Restore your files from an earlier date, 3. Lose your data and cry. We have worked on this virus for other companies and we ended up restoring the data piece by piece, which took 11 hours but it was less time than just doing a full restore. Be glad that some one put forth the effort to remedy this virus, for free.
If you are having trouble with Viruses, Computer Issues or Network Administration, let us know.